OpenVidu Single Node PRO installation: AWS#
Info
OpenVidu Single Node Pro is part of OpenVidu PRO. Before deploying, you need to create an OpenVidu account to get your license key. There's a 15-day free trial waiting for you!
This section contains the instructions to deploy a production-ready OpenVidu Single Node PRO deployment in AWS. Deployed services are the same as the On Premises Single Node installation but automate the process with AWS CloudFormation.
First of all, import the template in the AWS CloudFormation console. You can click the following button...
...or access your AWS CloudFormation console and manually set this S3 URL in the Specify template section:
https://s3.eu-west-1.amazonaws.com/get.openvidu.io/pro/singlenode/latest/aws/cf-openvidu-singlenode.yaml
Info
If you want to deploy a specific version of OpenVidu Single Node, replace latest with the version you want to deploy. For example, to deploy version 3.5.0, use the following URL:
CloudFormation Parameters#
Depending on your needs, you need to fill the following CloudFormation parameters:
Domain and SSL Certificate Configuration#
There are three possible scenarios for this section:
If you don't have a Domain Name and want to quickly test OpenVidu on AWS, you can use this option, simply selecting the CertificateType as letsencrypt and keep the rest of parameters empty.
It will deploy OpenVidu with a Let's Encrypt certificate generated using sslip.io based on the public IP created for the deployment.
sslip.io rate limiting
sslip.io is currently experiencing Let's Encrypt rate limiting issues, which may prevent SSL certificates from being generated. It is recommended to use your own domain name. Check this community thread for troubleshooting and updates.
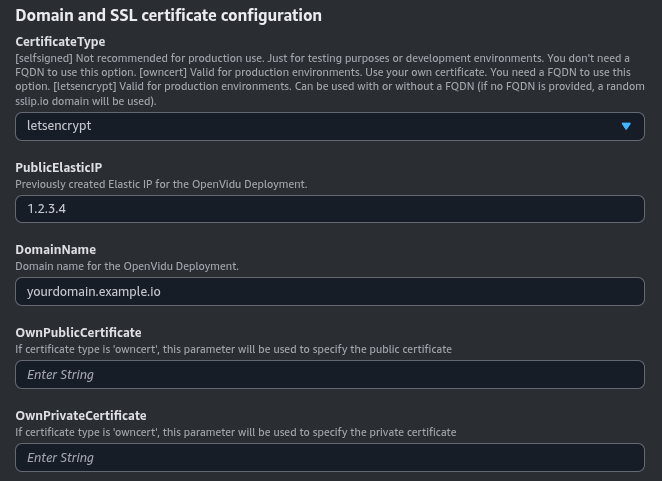
For a production environment, it is highly recommended to use this option. It allows you to deploy OpenVidu on AWS with a valid Let's Encrypt certificate for your Fully Qualified Domain Name (FQDN).
You need to previously create an Elastic IP and have a Domain Name pointing to that Elastic IP.
You can specify the DomainName with your FQDN and optionally the PublicElasticIP with the Elastic IP that the domain points to.
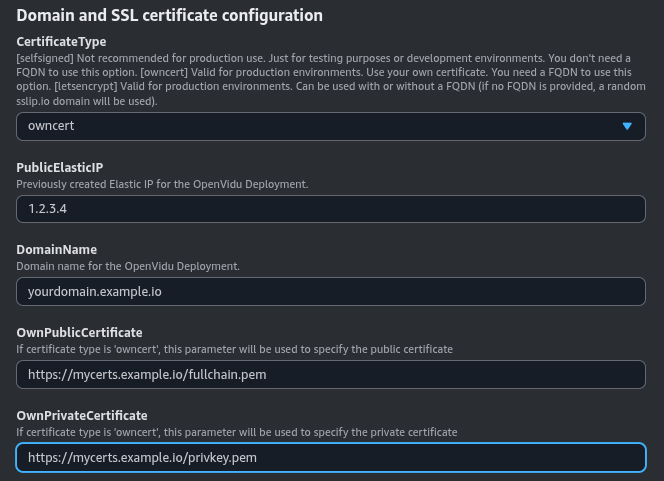
Opt for this method if you possess your own certificate for an existing FQDN. It enables you to deploy OpenVidu on AWS using your certificates.
You need to have a Fully Qualified Domain Name (FQDN) pointing to a previously created Elastic IP.
Also, you need a temporary HTTP server hosting your private and public certificate under a specific URL. These URLs are needed for the instance to be able to download and install your certificates.
The configured parameters would look like this:
You need to specify at OwnPublicCertificate and OwnPrivateCertificate the certificates files in base64. The DomainName and PublicElasticIP are mandatory parameters.
Certificates need to be in PEM format and base64 encoded. You can encode them using the following command in a terminal where fullchain.pem is your public certificate and privkey.pem is your private certificate:
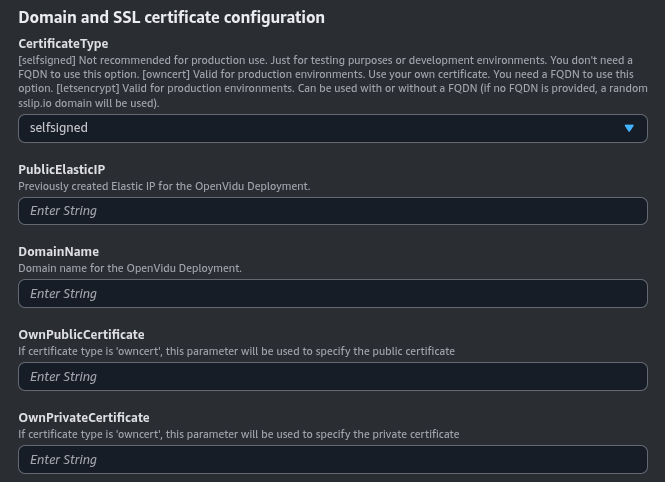
This option is useful for development and testing purposes. It allows you to deploy OpenVidu on AWS with an autogenerated self-signed certificate. This way, you can quickly set up a secure connection without the need to obtain a certificate from a trusted Certificate Authority (CA).
However, this convenience comes with the caveat that users will need to manually accept the certificate in their web browsers. Please be aware that this configuration is solely for developmental and testing purposes and is not suitable for a production environment.
These are the parameters needed in this section to use self-signed certificates:
You can optionally specify a DomainName. If no domain name is provided, sslip.io{:target="blank"} will be used to generate a domain based on the public IP. Just select the CertificateType as _self-signed.
OpenVidu Single Node PRO configuration#
In this section, you need to specify some properties needed for the OpenVidu Single Node PRO deployment.
Parameters of this section look like this:
Make sure to provide the OpenViduLicense parameter with the license key. If you don't have one, you can request one here.
For the RTCEngine parameter, you can choose between Pion (the default engine used by LiveKit) and Mediasoup (with a boost in performance). Learn more about the differences here.
OpenVidu Meet Credentials#
Configure the initial credentials for accessing OpenVidu Meet:
Parameters in this section look like this:
- InitialMeetAdminPassword: Initial password for the "admin" user in OpenVidu Meet. If not provided, a random password will be generated and stored in the AWS Secret Manager.
- InitialMeetApiKey: Initial API key for OpenVidu Meet. If not provided, no API key will be set and the user can configure it later from the Meet Console.
Both parameters are optional. If you don't specify them, you can retrieve the generated credentials from the AWS Secret Manager after deployment.
EC2 Instance Configuration#
You need to specify some properties for the EC2 instance that will be created.
Parameters in this section look like this:
Simply select the type of instance you want to deploy at InstanceType, the SSH key you want to use to access the machine at KeyName, and the Ubuntu distribution you want to use at OperatingSystem.
By default, the parameter OperatingSystem is configured to use the latest LTS Ubuntu AMI, so ideally you don’t need to modify this.
S3 bucket for application data and recordings#
You can specify an S3 bucket to store the recordings and application data. If this parameter is not specified, a new S3 bucket will be created by the CloudFormation stack.
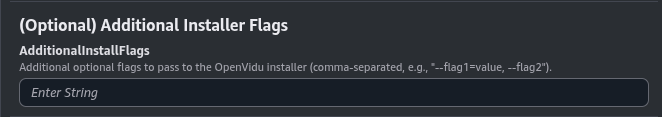
(Optional) Additional flags#
Additional optional flags to pass to the OpenVidu installer (comma-separated, e.g., --flag1=value, --flag2).
Parameters in this section look like this:
For example, you can use --experimental-turn-tls-with-main-domain to use the same domain as the main one for the TURN server with TLS, instead of specifying a different one in the TURN server configuration with TLS section.
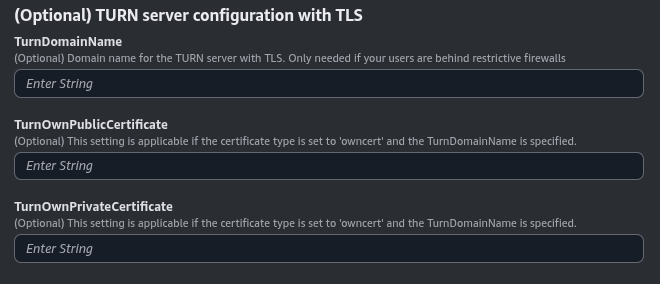
(Optional) TURN server configuration with TLS#
This section is optional. It is useful when your users are behind a restrictive firewall that blocks UDP traffic. This parameter will only work if you are using letsencrypt or owncert as the CertificateType parameter.
Note that if you are not using any Domain Name in the Domain and SSL Certificate Configuration section, this section will be ignored and a generated domain based on the public IP and sslip.io will be used instead.
Parameters in this section look like this:
Set the TurnDomainName parameter to the domain name you intend to use for your TURN server. It should be pointing to the PublicElasticIP specified in the previous section.
If you are using letsencrypt as the CertificateType parameter, you can leave the TurnOwnPublicCertificate and TurnOwnPrivateCertificate parameters empty. If you are using owncert, you need to specify the base64 encoded certificates for the TURN server in these parameters.
Deploying the stack#
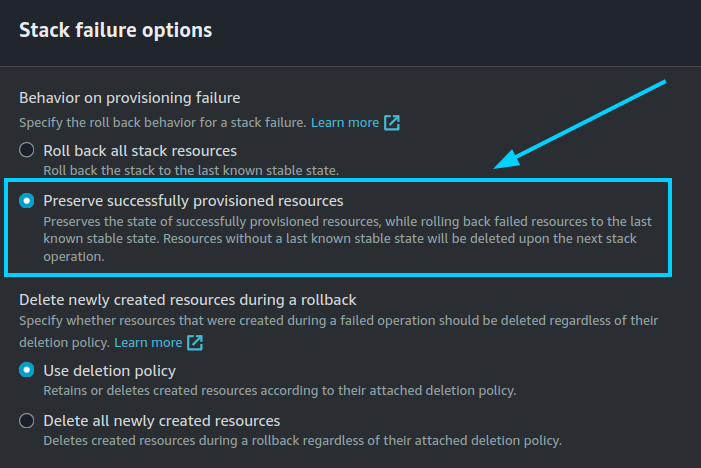
When you are ready with your CloudFormation parameters, just click on "Next", specify in "Stack failure options" the option "Preserve successfully provisioned resources" to be able to troubleshoot the deployment in case of error, click on "Next" again, and finally "Submit".
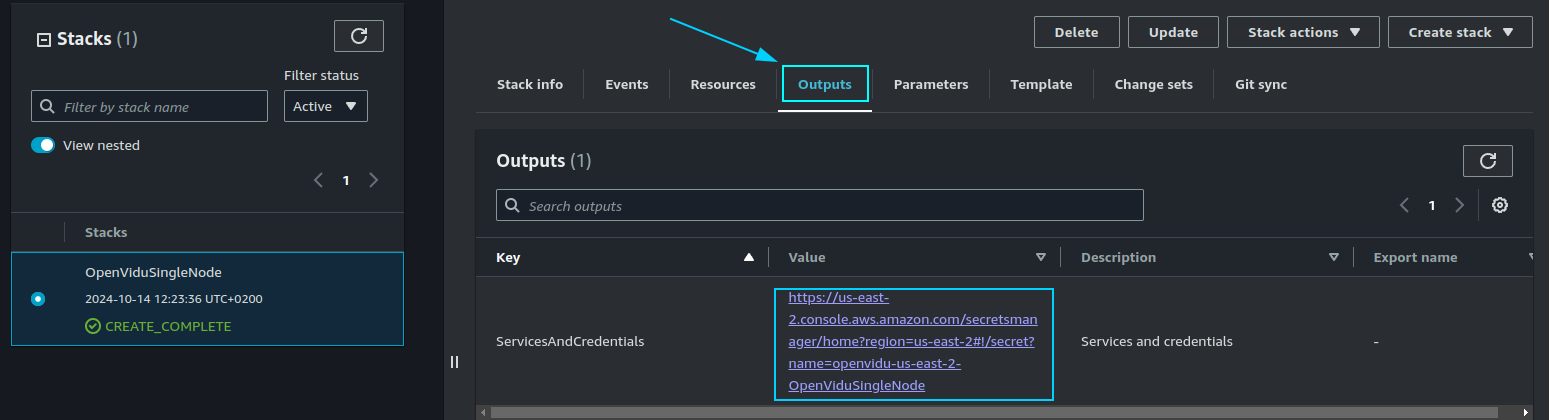
When everything is ready, you will see the following links in the "Outputs" section of CloudFormation:
Configure your application to use the deployment#
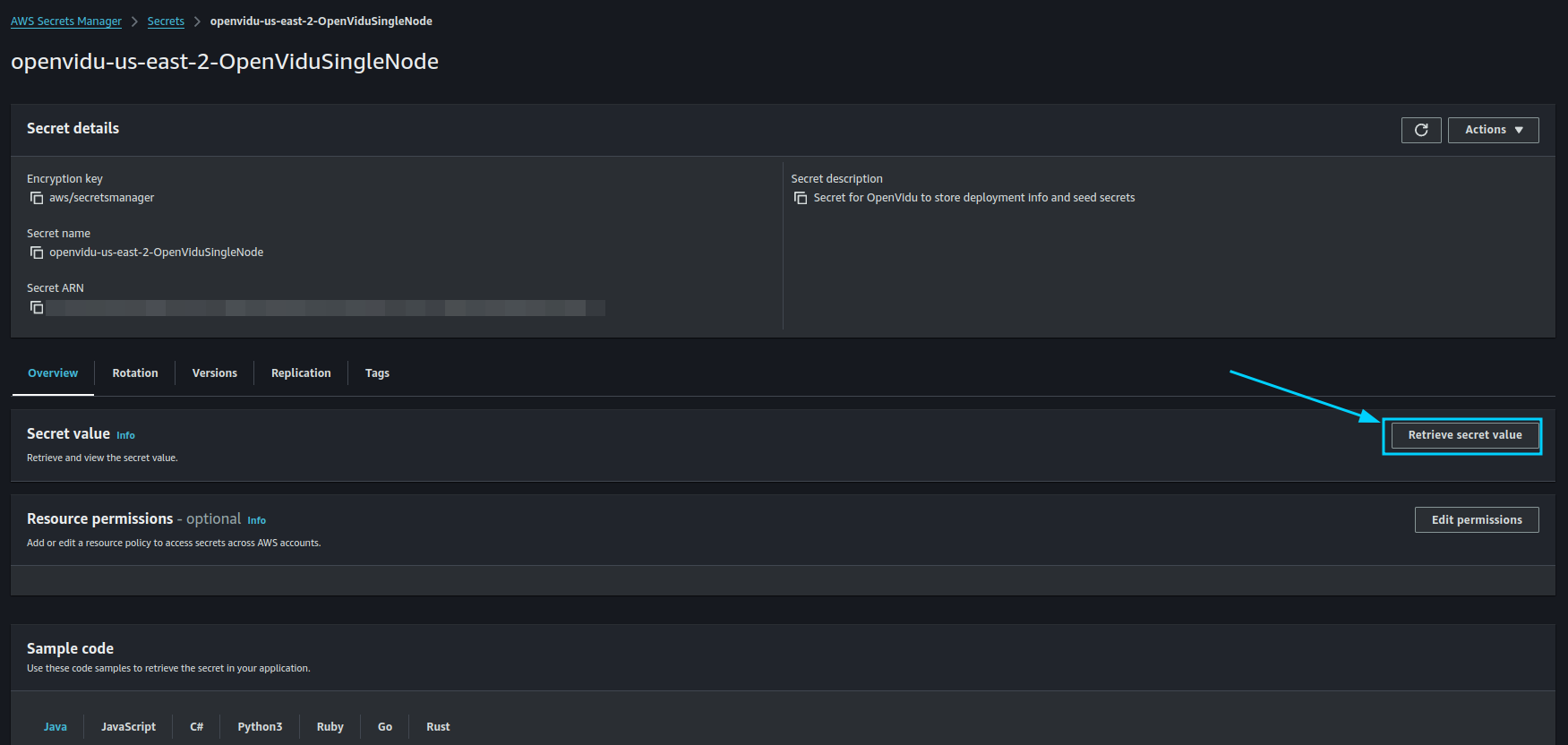
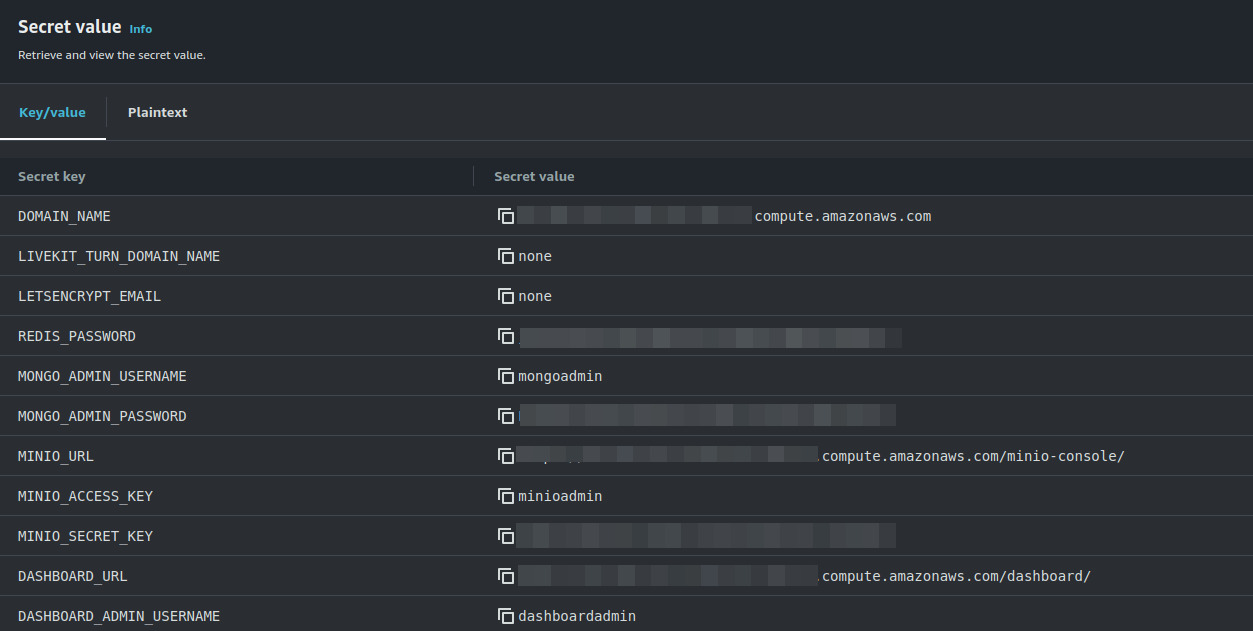
The Output Key ServicesAndCredentials of the previous section points to an AWS Secret Manager secret that contains all URLs and credentials to access the services deployed. You can access the secret by clicking on the link in the Output Value column.
Then, click on Retrieve secret value to get the JSON with all the information.
To use your OpenVidu deployment, check the values of the JSON secret. All access credentials of all services are defined in this object. The most relevant ones are:
OpenVidu Meet:
OPENVIDU_URL: The URL to access OpenVidu Meet, which is alwayshttps://yourdomain.example.io/MEET_INITIAL_ADMIN_USER: User to access OpenVidu Meet Console. It is alwaysadmin.MEET_INITIAL_ADMIN_PASSWORD: Password to access OpenVidu Meet Console.MEET_INITIAL_API_KEY: API key to use OpenVidu Meet Embedded and OpenVidu Meet REST API.
Note
The MEET_INITIAL_ADMIN_USER, MEET_INITIAL_ADMIN_PASSWORD, and MEET_INITIAL_API_KEY values are initial settings that cannot be changed from AWS Secret Manager. They can only be changed from the Meet Console.
OpenVidu Platform:
LIVEKIT_URL: The URL to use LiveKit SDKs, which can bewss://yourdomain.example.io/orhttps://yourdomain.example.io/depending on the client library you are using.LIVEKIT_API_KEY: API Key for LiveKit SDKs.LIVEKIT_API_SECRET: API Secret for LiveKit SDKs.
OpenVidu V2 Compatibility Credentials
This section is only needed if you want to use OpenVidu v2 compatibility.
- URL: The URL to access OpenVidu, which is the value of
OPENVIDU_URL(e.g.,https://yourdomain.example.io/) - Username: Basic auth user for OpenVidu v2 compatibility. It is always
OPENVIDUAPP. - Password: Basic auth password for OpenVidu v2 compatibility is the same as
LIVEKIT_API_SECRET.
Troubleshooting Initial CloudFormation Stack Creation#
If something goes wrong during the initial CloudFormation stack creation, your stack may reach the CREATE_FAILED status for multiple reasons. It could be due to a misconfiguration in the parameters, a lack of permissions, or a problem with the AWS services. When this happens, the following steps can help you troubleshoot the issue and identify what went wrong:
-
While deploying the stack, make sure at "Stack failure options" you have selected the option "Preserve successfully provisioned resources" to be able to troubleshoot the deployment in case of an error.
-
Check if the EC2 instance or instances are running. If they are not, check the CloudFormation events for any error messages.
-
If the EC2 instance or instances are running, SSH into the instance and check the logs of the following files:
/var/log/cloud-init-output.log/var/log/cloud-init.log
These logs will give you more information about the CloudFormation stack creation process.
-
If everything seems fine, check the status and the logs of the installed OpenVidu services.
Configuration and administration#
When your CloudFormation stack reaches the CREATE_COMPLETE status, your OpenVidu Single Node deployment is ready to use. You can check the Administration section to learn how to manage your deployment.